External Identities in Microsoft Entra
This blog article aims to give Microsoft 365 administrators an overview of the External Identities section in Entra (formerly Azure Active Directory or Azure AD).
Entra External Identities refers to a collection of features designed to help businesses securely handle and oversee users who aren’t part of their organization, such as clients or business partners. These features expand upon the B2B (business-to-business) collaboration tools available in Microsoft Entra ID by offering more options for engaging and establishing connections with users from outside your company. Essentially, it’s about making it easier and safer to interact with people who need access to certain parts of your IT environment but aren’t your employees.
Read this case study if you would like to find out how machine manufacturer GROB automated guest management in M365.
In this blog post, we take a look at the External Identities features in the Microsoft Entra Admin Center at https://entra.microsoft.com/.
While Entra covers most topics around guests, several important settings can be found in various other Microsoft Admin Centers.
This is where External User Manager can help: it is a comprehensive tool designed to simplify the management of external identities in Microsoft 365 by combining all security and compliance features in one easy-to-use app.
What is possible with External Identities in Microsoft Entra?
You can find the Entra External ID features by following these steps:
Once you have opened Entra or the Entra Admin Center, select the item „External Identities“ in the navigation menu on the left, just below „Identity Governance“.
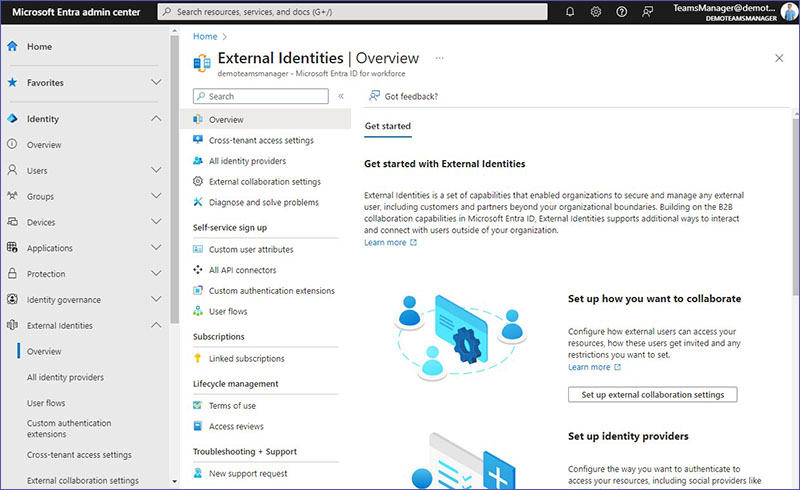
The option “Overview” is the starting point when working with External Identities and gives an outline of the different sub-bullets.
In addition to the main navigation points, there are also three additional topics included and linked to:
Invite exteral users to collaborate
Here you can find a list of all users in your tenant and can invite new external users.
For setting up a customized invitation process with automated approval workflows, External User Manager is the tool for you.
Set up Conditional Access policy to protect your applications & brand
Use advanced security features within Microsoft Entra Conditional Access to control how external users access your applications and data, ensuring they comply with your company’s security standards.
Manage provisioning & access and set up access reviews
Identity Governance offers the tools necessary for managing external users. It streamlines the process of adding (onboarding) and removing (offboarding) these users through Entitlement Management. Additionally, Access Reviews can be set up to verify that only those who still need access have it, ensuring proper control over who gets to access what within your organization.
For provisioning and access management, External User Manager automates the onboarding of external users as well as the offboarding process. Admins can set up lifecycles for external users, including periodic access reviews for continuous compliance or even automated removal from the tenant and the AD / Entra.
What can you find under “All identity providers”?
Decide on options for how users authenticate their identities to access your resources. This includes using accounts from social networks like Facebook and Google.
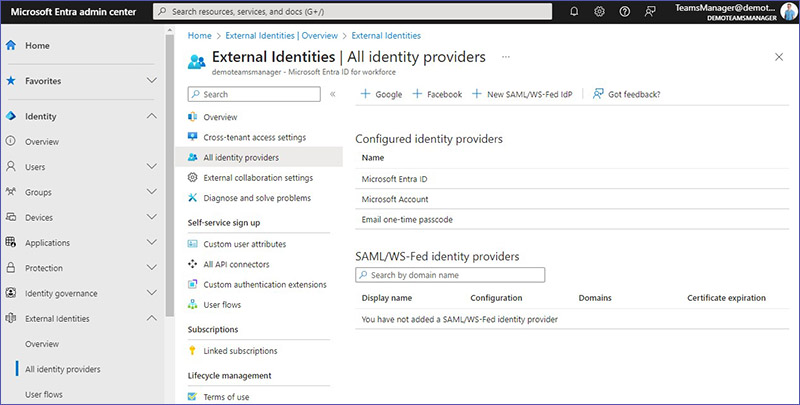
Configured identity providers
Microsoft Entra ID
Users with a Microsoft Entra account can be invited to access your resources through email. They can log in directly without needing further setup. They also have the option to register themselves through Self-service sign-up and User flows.
Microsoft Account
Similar to a Microsoft Entra account, users with a Microsoft account can be invited and log in without extra steps. They too can use Self-service sign-up with User flows for registration.
Email one-time passcode
This option is for users who don’t have a Microsoft Entra or Microsoft account. They can access your environment by receiving a one-time passcode via email each time they need to sign in, avoiding the need to create a new account. This method can also be used for self-service sign-up for specific applications within your user flows.
SAML/WS-Fed identity providers
SAML (Security Assertion Markup Language)
This is a standard used for exchanging authentication and authorization data between parties, e.g. between an identity provider and a service provider. By using SAML, users can sign in to multiple applications with one set of credentials managed by their organization. It’s widely used for single sign-on (SSO) processes to access web applications, e.g. bei AWS (Amazon Web Services) or Okta.
WS-Fed (WS-Federation)
Similar to SAML, WS-Federation is a protocol used for federated identity and access management. It allows different organizations to use their existing identity management processes to authenticate users without exposing sensitive information. WS-Fed is often used in corporate environments for seamless access across a range of applications and services. Single Sign-On with WS-Fed is supported by OneLogin, for example.
How can you set up user flows in Entra?
A self-service sign-up user flow lets you set up a system where people outside your organization can register themselves to use your applications. This means you can design a registration process tailored to your needs, allowing external users, like customers or partners, to create accounts and gain access to your apps without needing direct assistance from your IT team.
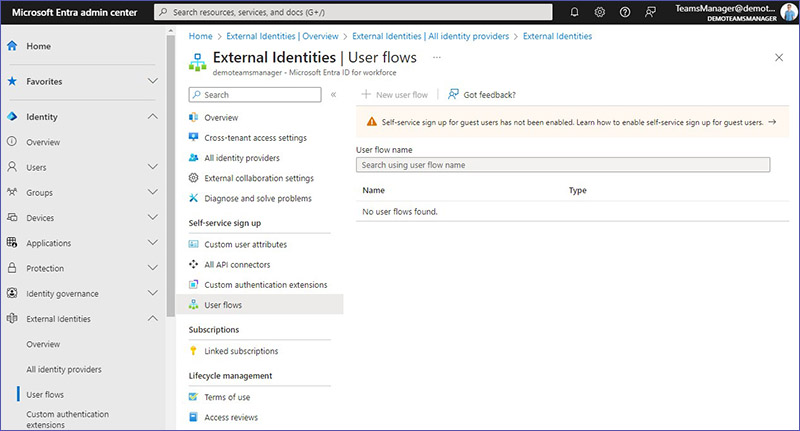
Please note: Self-service sign-up for guests needs to be enabled before you can create user flows.
- Read more about User Flows in Microsoft Learn
What are custom authentication extensions in Entra?
Custom authentication extensions enable you to personalize how users log into Microsoft Entra by connecting it with outside systems. If you want to employ a special method for users to sign in or verify their identity that isn’t provided out of the box, these extensions allow you to build that custom process using web APIs.
- Find out more about Custom Authentication Extensions at Microsoft Learn
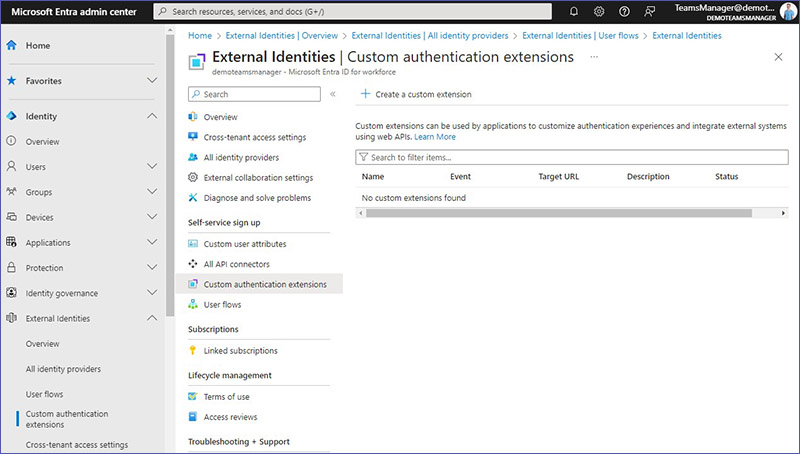
What is possible with cross-tenant access settings?
Organizational Settings
Cross-tenant access settings in Microsoft Entra enable you to tailor how your organization interacts with selected external Microsoft Entra tenants. When dealing with entities that don’t utilize Microsoft Entra, adjust your general collaboration settings instead.
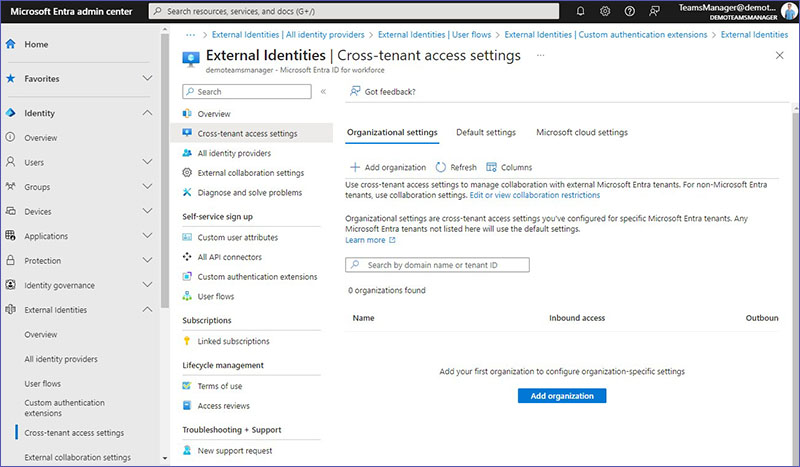
Organizational settings within this context refer to the specific access permissions and policies you’ve established for certain Microsoft Entra environments with which you collaborate. These settings ensure that your collaboration rules are applied precisely to those entities. For any Microsoft Entra environments not explicitly covered by these bespoke settings, your organization’s default settings will automatically apply.
- See what Microsoft Learn has to say about Organizational Settings for Cross Tenant Access
The detailed settings can be found under External Collaboration Settings.
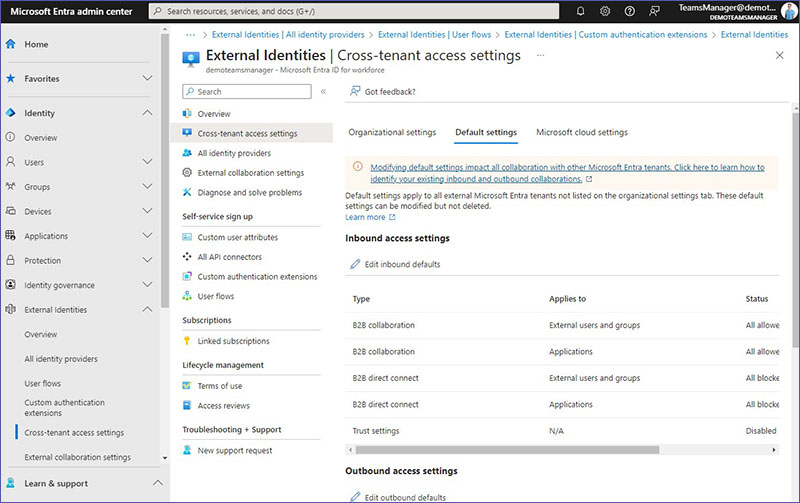
Default Settings
In Microsoft Entra, the default settings act as a baseline for how your organization interacts with any external Microsoft Entra environments that you haven’t specified under the organizational settings tab. While you can change these default settings to better suit your organization’s security or collaboration needs, you cannot remove them entirely. This ensures there’s always a predefined way your system handles interactions with any external Microsoft Entra tenants not explicitly covered by your customized settings.
- Read more about the Default Settings for cross-tenant access in Microsoft Learn
Default Inbound access settings
This section offers different ways you can manage access for external users into your Microsoft Entra environment, focusing on how to control this access and the type of user experience you want to provide.
Inbound access settings for type: B2B collaboration
Default Inbound Access Settings for B2B Collaboration allow you to work with individuals from outside your organization by letting them use their own credentials to sign in. These external users are treated as guests within your Microsoft Entra tenant. You can either invite these external users manually or enable a self-service registration process, allowing them to request access on their own. You can specify whether to allow or deny access to these users for certain apps or all apps within your environment and set the order in which primary identity providers and fallback identity providers are used.
Inbound access settings for type: B2B direct connect
This setting is about enabling a more seamless connection with users from other Microsoft Entra tenants, allowing them access to your resources without the need to add them as guests. By opting to “Allow access,” you open the door for users and groups from other organizations to connect with your resources directly, provided the other party has also enabled B2B direct connect.
Trust settings
These settings relate to how your Conditional Access policies treat claims from other Microsoft Entra tenants. Essentially, you can decide whether to trust multifactor authentication, compliant devices, and Microsoft Entra hybrid joined devices from external tenants. This trust is critical for enforcing your security policies when external users access your resources. The default trust settings apply universally, except for those external tenants you’ve configured with specific organizational settings. To enhance Microsoft 365 security for guest access, you might require multifactor authentication or device compliance across all cloud apps.
Default Outbound access settings
Configure outbound access for your users, detailing how they can interact with external organizations via Microsoft Entra, with a focus on B2B (business-to-business) collaboration and B2B direct connect settings.
- Microsoft Learn has more details about Default Outbound Access Settings
Outbound access settings for type: B2B collaboration
B2B collaboration outbound access settings control whether your users can be invited to collaborate with external Microsoft Entra tenants, essentially allowing them to be added to these external directories as guests. These settings are the default for all external tenants unless you’ve created specific settings with certain tenants. Here, you determine if your users and groups can be invited to these external entities and which external applications they are allowed to access.
Outbound access settings for type: B2B direct connect
These settings manage the ability of your users and groups to access applications and resources hosted by external organizations. The default configuration is applied across all situations where your users interact with external tenants unless you’ve specified different settings for particular external organizations. Although these default settings can be altered to fit your needs, they cannot be entirely removed.
- Take a look at B2B Direct Connect for Outbound Access Settings in Microsoft Learn
B2B direct connect determines your users’ and groups’ access to resources in another organization. For this access to be granted, an administrator on the external side must also have B2B direct connect enabled. When you activate this feature, a limited amount of your users’ information is shared with the external organization to allow for functionalities like user search. The amount of data shared can increase if your users agree to the privacy policies of the external organization.
- Here is another article in Microsoft Learn providing a good overview of B2B direct connect
Default Tenant restrictions
Tenant restrictions are about setting up rules within your network to control if and how your users can use external applications with non-company accounts. This includes both accounts given to them by other organizations and personal accounts they’ve created under other Microsoft Entra tenants. You can specifically allow or deny access to certain external applications.
These default settings are your baseline rules for dealing with all external Microsoft Entra tenants, unless you’ve crafted specific policies for particular tenants. Essentially, you’re setting a general policy that applies universally, with the option to tailor policies for specific external partners or services.
- Learn more about Default Tenant Restrictions
In this context, you can also develop detailed policies targeting specific scenarios, like access permissions for external users and groups or for certain external applications. This gives you granular control over how your organization interacts with external digital environments.
Microsoft Cloud settings
Microsoft cloud settings provide the capability to work together with entities located in various Microsoft cloud environments. Once you’ve activated these settings, you’re set to integrate organizations from those specific clouds into your collaboration efforts using Microsoft Entra’s B2B collaboration feature.
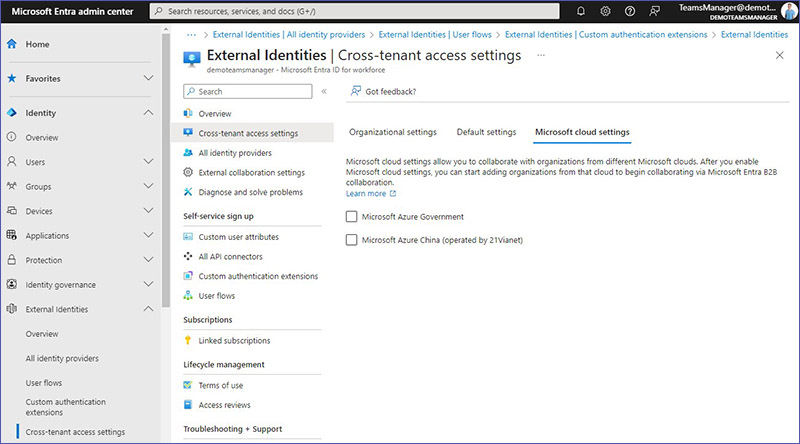
Here are the options you have:
Microsoft Azure Government
This is tailored for U.S. government agencies, providing a cloud environment that complies with U.S. government regulations.
Microsoft Azure China (operated by 21Vianet)
This is a version of Microsoft’s cloud services operated by 21Vianet within China, designed to comply with Chinese regulatory requirements.
By utilizing these settings, you enable your organization to establish and manage secure collaboration channels with partners operating in these distinct Microsoft cloud environments.
- Here is more information about the Microsoft Cloud Settings
How can you configure external collaboration settings?
Configure the rules and permissions for how external users can interact with your organization’s resources, i.e. how they are invited, what they can access, and any limitations on their activities.
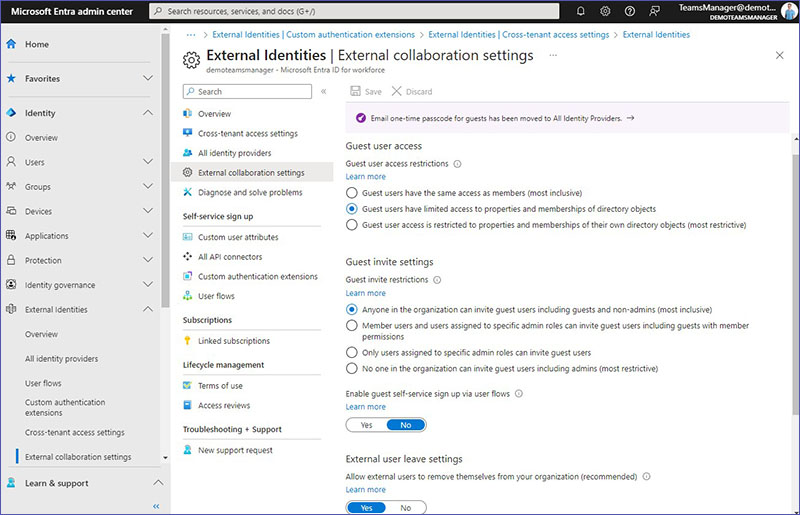
Guest user access
Choose the level of access restrictions for guest user access best suited for your organization:
- Grant them the same rights as full members (broadest access).
- Allow them limited access to and interaction with directory objects.
- Restrict their access to only viewing and interacting with their own directory objects (tightest control).
Guest invite settings
This determines who in your organization is able to invite guest users to your directory for collaboration on e.g. SharePoint sites or Azure resources. Choose which of these guest invite restrictions best matches your requirements. In this section, you can also enable or disable guest self-service sign up via user flows.
- Allow everyone, including current guests and non-administrators, to send invites (most open).
- Limit invitation rights to members and certain admins, including guests with member rights.
- Restrict this capability solely to users in specific administrative roles.
- Block anyone in the organization from inviting guests (strictest setting).
In this section, you can also toggle on or off the ability for guests to sign up for access on their own through user flows.
External user leave settings
Here you can allow external users to remove themselves from your organization or block them from doing so.
Enabling this settings means that external users can remove themselves from your organization without needing admin approval. Disabling it requires them to consult a privacy statement or contact a privacy officer for permission to leave, adding an extra layer of control.
Collaboration restrictions
These settings impact the cross-tenant invitation process by setting rules based on the recipient’s domain:
- Allow invitations to any domain for the most inclusive approach.
- Block invitations to specific external domains to prevent access from certain organizations, thus creating a blacklist of external domains.
- Only allow invitations to specific approved target domains for the most controlled environment, thus creating a whitelist of approved external domains.
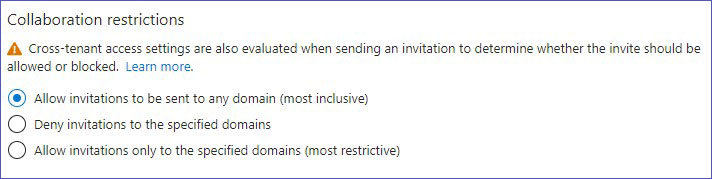
External User Manager provides detailed controls for managing access between different tenants, ensuring the security and efficiency of cross-tenant collaborations. Administrators can set specific policies for external access and also create blacklists and whitelists for entire external domains.
How can you connect different tenants with cross-tenant synchronization?
Cross-tenant synchronization is a capability within Microsoft Entra ID designed to streamline the management of user identities across different tenants within your organization. This feature focuses on easing the collaboration process by ensuring that user identities are consistent and up-to-date across various tenants.
Automated Provisioning
Set up automatic processes for creating and managing user identities across your organizational tenants. This simplifies the onboarding process for new users and ensures everyone has access to the necessary resources without manual intervention.
Seamless Collaboration
By maintaining synchronized identities, users can more easily collaborate across different parts of your organization, even if those parts are managed as separate tenants.
Account Lifecycle Management
Automate the process of deactivating accounts when they’re no longer needed and keep user accounts synchronized to reflect any changes in their status or roles within the organization.
Cross-tenant synchronization supports scenarios such as:
B2B User Management
Automatically create user accounts across tenants for B2B scenarios, or enrich B2B user profiles with data from their primary (home) tenant.
Application Sharing
Facilitate the sharing of applications across tenants, utilizing the identity and access management (IAM) capabilities of Microsoft Entra ID to control access securely.
- Microsoft Learn provides an overview of Cross Tenant Synchronization here
Initiate the process by creating a new configuration. This involves setting up rules and processes for automatically managing the identity lifecycle within Microsoft Entra, including the creation, updating, and deletion of user accounts as people join, move within, or leave your organization.
- For more details, take a look at the full documentation for application and HR provisioning
Complicated admin centers – or one comprehensive app
External User Manager offers a comprehensive solution for guest management in Microsoft 365 that goes beyond the native features of Microsoft Entra and the other admin centers. External User Manager provides an intuitive interface for the automation of invitations and access reviews and significantly reduces the administrative effort required to manage external identities.
Its capabilities for detailed access control and security compliance ensure that organizations can maintain high security standards while still staying open to collaboration. Book a free demo to find out more!
Interested in easily managing External Identities?

Head of Marketing & Sales at Solutions2Share – Florian Pflanz has 6 years of M365 experience and has been involved in numerous projects concerning Microsoft Teams governance. In over 200 workshops, he has collected extensive knowledge and best practices regarding Microsoft Teams and companies’ management requirements.





This is a great overview of the External Identities section in Microsoft Entra! It’s helpful to see how these tools can make it easier to manage external users securely. I especially appreciate the mention of the External User Manager as a way to consolidate all the security and compliance features into one interface – that’s a game-changer for admins trying to streamline the process. The case study with GROB is a nice touch, too, showing how real businesses are leveraging these features. Looking forward to diving deeper into the Admin Center to explore all these options!
Thank you James for your great feedback!
We’re glad we can help you with our blog post and wish you every success in the Admin Center.
Best regards
Solutions2Share